Single sign-on
Go to the Configuration menu.
Select Single Sign On.
Single sign-on (SSO) can make accessing Tesults more secure and convenient for team members. Tesults supports SAML 2.0 and Google OAuth. Both options are detailed below.
SAML 2.0
This option should be used if your organization uses an identify provider such as Microsoft's Active Directory, Azure AD, Okta, OneLogin, LastPass, Bitium, SecureAuth and other identity providers supporting SAML 2.0.
Setup SAML based single sign-on from the config menu.
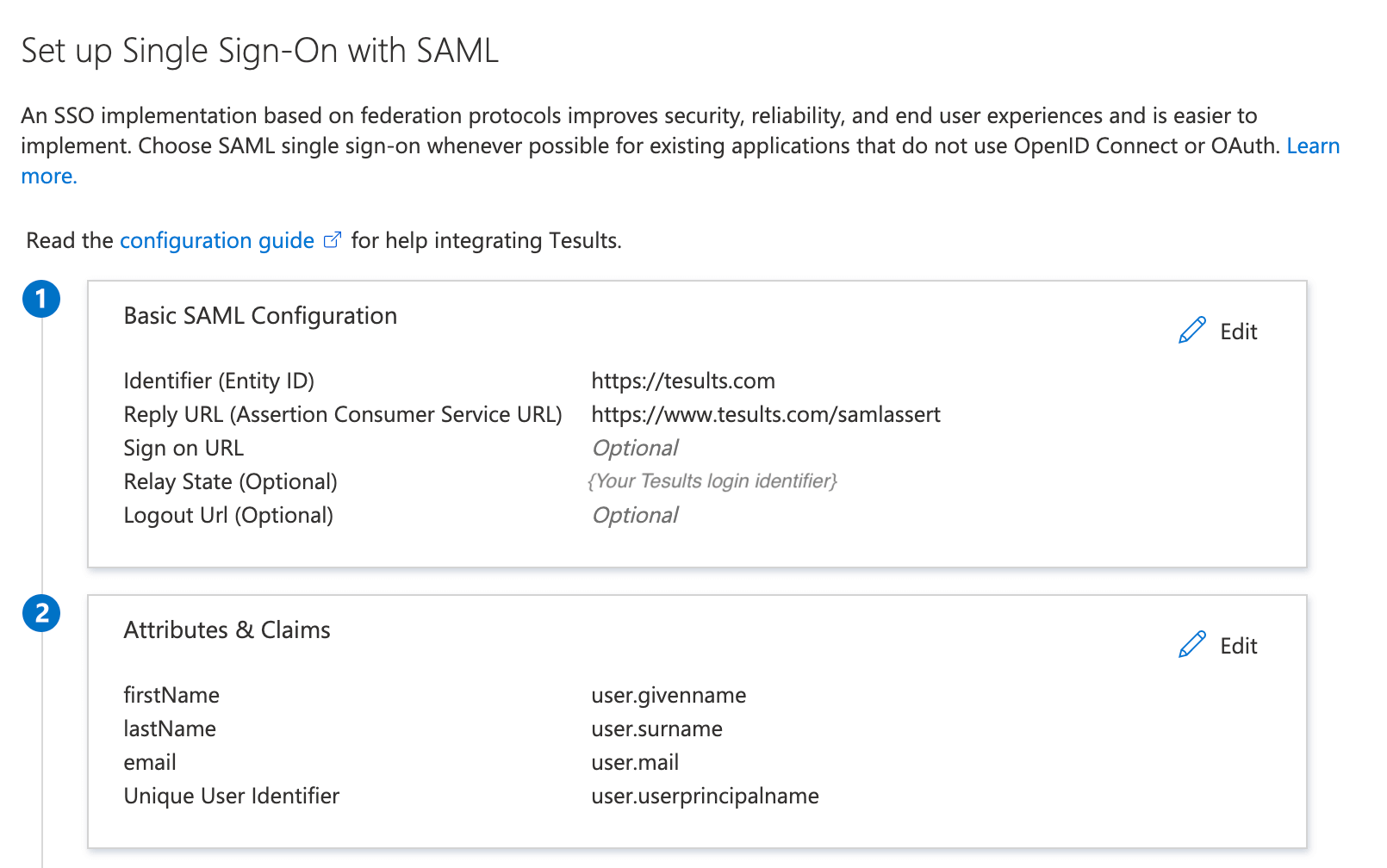
Ensure the selected project is the one you want to configure and then click 'Single sign-on (SSO)' and select SAML.
Select an identifier
If you have not enabled single sign-on before you will be asking to select an identifier. This identifier will be used as part of your single sign-on login url so pick something that makes sense to your team, speciifically the login link format will be: https://www.tesults.com/login/<identifier>
Input identity provider information
Three pieces of information are needed from your identify provider:
- Login endpoint
- Identity provider entity ID
- Public X.509 certificate
Your can get all of this information from your single sign-on provider. If you would like more details or help gathering this information please contact help@tesults.com.
Configure identify provider
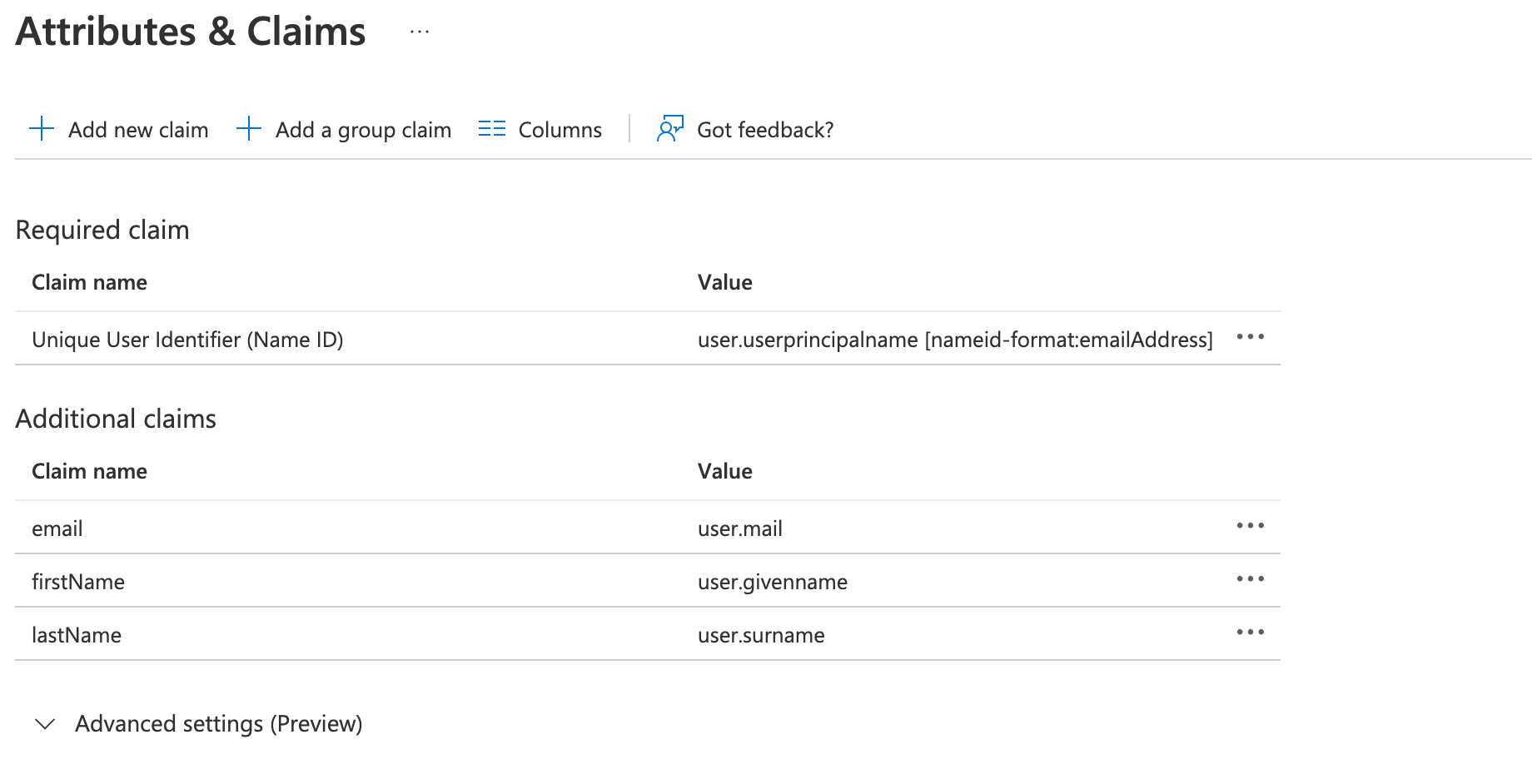
Configure three attribute statements on your identify provider's (single sign-on provider) interface:
- email - mapped to the email of a user
- firstName - mapped to the first name of the user
- lastName - mapped to the last name of a user
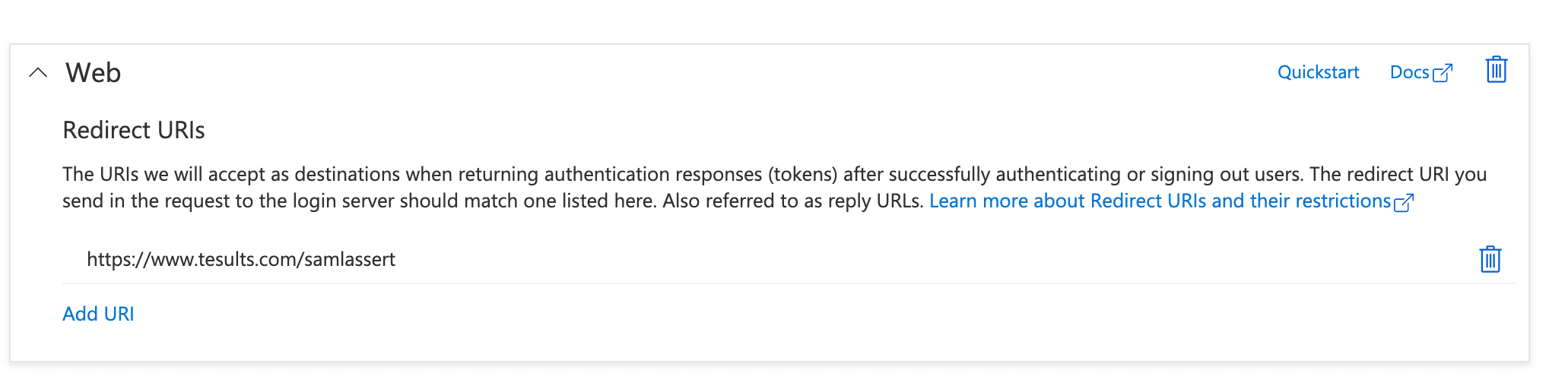
Set the login endpoint (saml assert) to https://www.tesults.com/samlassert and the 'audience' value to be the identifier you selected (as described above, it forms part of your login endpoint).
Optionally if you want to allow team members to automatically access Tesults by following a link from within your single sign-on provider's interface (identify provider initiated requests) then ensure you set the default relay state to your identifier.
Also optional, you can download Tesult's public encryption key if you want to configure end-to-end encryption. Keep in mind all requests are already made using TLS and will be encrypted so this is not required.
Enable SAML SSO
At this point you can enable single sign-on. Now your team members can sign in using your single sign-on link without creating Tesults login credentails and you get all of the benefits of SSO such as being able to revoke access from your identify provider.
Other options
Once single sign-on is enabled you can choose to:
- Disable login with Tesults credentials
- Disable email address change
- Disable Tesults project creation
We recommend disabling the first two for security reasons, but only once you have ensured the SAML configure is correct and the sign on flow has been tested. The third option should be set depending on whether you want users to be able to create their own projects.
Please contact support if you encounter issuess getting SAML configured.
Azure AD Note

SCIM
SCIM is currently unsupported. Please let us know at help@tesults.com if this is something you are interested in.
Google OAuth
If your organization uses Google Workspace you can enable sign in using Google OAuth.
Setup sign-in using Google from the config menu.
Ensure the selected project is the one you want to configure and then click 'Single sign-on (SSO)' and then select Google OAuth.
Select an identifier
If you have not enabled single sign-on before you will be asking to select an identifier. This identifier will be used as part of your single sign-on login url so pick something that makes sense to your team, speciifically the login link format will be: https://www.tesults.com/login/<identifier>
Authorize by email domain or specific emails only
You can choose to authorize access to the project either by adding specific email addresses in the team members configuration page or by allowing email addresses matching particular domains.
Enable sign-in with Google
Click the Enable Google SSO button to enable sign-in using Google.